SSL/TLS certificates are the backbone of modern website security. They ensure that the data exchanged between your server and visitors is encrypted and protected from malicious actors.
But not all SSL/TLS certificates are created equal. For those looking for a quick and cost-free solution, self-signed SSL certificates can be an attractive choice. However, as the saying goes, there’s no such thing as a free lunch. These self-signed certificates come with significant limitations and risks, especially for public-facing websites.
In the following article, we’ll delve into what a self-signed certificate is, how it differs from certificates issued by trusted Certificate Authorities (CAs) and why using one on your website is a bad choice. With that said, we’ll also cover the small number of use cases where a self-signed certificate might be a suitable option.
What is a Self-Signed Certificate?
As the name suggests, a self-signed SSL certificate is issued and signed by the same entity (website) that is using it instead of being validated and signed by a trusted third-party Certificate Authority (CA).
When you generate a self-signed SSL certificate, it contains all the same components as one traditionally issued by a CA (public key, private key, and metadata about the validity of the certificate and who it belongs to.)
The fundamental difference between a self-signed certificate and one issued by a CA is, you guessed it, the signature. Rather than being signed by a widely known and established third-party CA (like Comodo, Verokey, Thawte, etc.), the signature is generated using your own private key.
What’s the Problem with Using a Self-Signed Certificate?
The fact that they are not validated and signed by a third-party CA inherently makes self-signed SSL certificates less trustworthy, even though they still enable HTTPs.
Using a self-signed certificate to secure your website would be like creating your own driver’s license and expecting everyone else to trust it. When the government issues you a driver’s license, it goes through a verification process that establishes your identity and confirms your qualifications to drive. People trust this because your license is backed by a credible, recognised organisation.
You might be able to print your own license at home that looks authentic, but nobody will recognise or trust it – even if you really do know how to drive.
In the same way, a self-signed SSL certificate does not benefit from any external validation. So, while the certificate may technically work to encrypt data, browsers, and by extension, users, can’t be sure it’s genuine or secure.
This defeats one of the main benefits of securing an SSL/TLS certificate in the first place – signalling trust so that people will interact with your website without worrying if their data is secure.
How Exactly Do Self-Signed Certificates Differ from CA-Signed Certificates?
Trust and Recognition
Because they are not backed by a recognised Certificate Authority, self-signed certificates lack the critical ‘Chain of Trust’ that is fundamental to why CA-signed certificates are valued.
For this reason, self-signed certificates are not inherently trusted by web browsers like Google Chrome or Microsoft Edge, meaning that users will get warning messages when trying to access your website (even if the certificate functionally works to encrypt data).
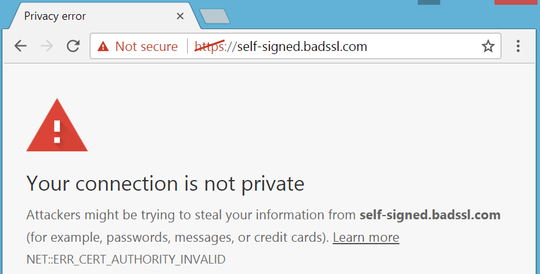
Validation
Our post on What is SSL describes the different levels of validation you can get with an SSL/TLS certificate. For example, a standard Domain Validated (DV) certificate verifies domain ownership, while a more robust Extended Validation (EV) certificate has rigorous checks that not only verify domain ownership but also the legal, operational, and physical existence of your business.
Self-signed certificates lack any type of external validation, meaning that there’s no guarantee to browsers and users that you are who you say you are.
Why You Might Use a Self-Signed Certificate
Despite numerous limitations, a self-signed certificate can have value in situations where trust isn’t a priority.
Here are a few examples:
Development Environments: Self-signed certificates can be a convenient way to test HTTPs locally or in a staging environment. Since these environments obviously aren’t accessible by the public, the lack of trust isn’t relevant.
Internal Networks: A self-signed certificate may be used by organisations within intranets or private file-sharing systems. Since all users are within a trusted network, third-party validation isn’t an issue.
Short-Term Projects/Demos: For any project where rapidly deploying HTTPs is the main concern, a self-signed certificate can deliver basic encryption. For example, perhaps you are building a prototype web app to demonstrate a new feature. While the app isn’t ready for public release, you want to showcase it in a secure environment using HTTPs.
While there are unboundedly many other examples where self-signed SSL certificates are valid, they are all similar in that user trust is a non-issue.
Step-by-Step Guide to Creating a Self-Signed SSL Certificate
Now that we’ve established some use cases for a self-signed SSL certificate let’s explain how you generate one.
First of all, to create a self-signed SSL certificate, most people will typically use the free and widely available tool Open SSL. Open SSL is an open-source toolkit with cryptographic functionalities, allowing users to generate private keys, create certificates, and test SSL/TLS connections.
Because of its flexibility and ease of use, Open SSL is the most popular option for self-signed SSL certificates. However, you can also turn to other options like Windows: PowerShell, Linux: mkcert, or Java: Keytool (for Java-based applications).
In this guide, we’ll assume you’re ok with using Open SSL to create your HTTPs certificate.
Install Open SSL: If you’re on Windows, you can simply download it from the OpenSSL website. For Linux users, you can find a tutorial here. You need to make sure you are using the latest OpenSSL binaries.
Generate a root private key: Run this command to generate a private key:
openssl genrsa -out privatekey.pem 2048
This generates a file named privatekey.pem with a 2048-bit RSA key.
Create a Certificate Signing Request (CSR): Use the private key to generate your CSR by running this command:
openssl req -new -key privatekey.pem -out request.csr
At this stage, you will be prompted to enter certificate details such as Common Name (your domain name), the name of your business or organisation/project, and a two-letter country code (such as AU or UK).
Generate your self-signed certificate: Run this command:
openssl x509 -req -days 365 -in request.csr -signkey privatekey.pem -out certificate.crt
The flag “-days 365” makes the certificate valid for one year, which is typical for most CA-signed certificates, but you can change this value to whatever you want.
Congratulations, you now have generated your own SSL certificate (certificate.crt). You can now install this certificate, in combination with your private key, on your web server and enable/test HTTPs.
Why Choose a Trusted Certificate Authority (CA) Instead?
Thanks to tools like OpenSSL, creating your own self-signed SSL certificate for free is relatively quick and straightforward. However, unless you fall into one of the aforementioned special use cases, you should avoid this route and purchase a genuine SSL/TLS certificate from a trusted CA.
While paying for a certificate and renewing it every one or two years is a downside, there’s simply no alternative if you want people to trust and engage with your website. As mentioned, without a valid certificate issued by a CA, browsers will warn users not to visit your website or will block it outright.
Additionally, your website will likely not even be discoverable by users without a CA-signed certificate. This is because search engines like Google place user trust and safety as one of their highest priorities, so they are unlikely to even show your website in search results if you don’t have a valid, independently verified certificate in place.
Luckily, at SSLTrust we make it easy to find affordable SSL/TLS certificates for whatever level of validation or functionality your website needs. If you’re unsure about anything, you can read our blog or visit our learning centre for comprehensive guides, or you can simply reach out to our support team for personalised guidance on selecting, installing, and managing your digital certificates.
Conclusion: Choosing the Right Certificate for Security and Trust
In conclusion, self-signed SSL certificates are a valid HTTPs solution for some niche uses. However, they should never be thought of as a free alternative to CA-signed certificates. For public-facing websites, self-signed certificates fall short in many of the key areas that really matter: browser trust, user confidence, and domain/business validation.
All of this highlights the importance of Certificate Authorities to the trust and security ecosystem of the web. With the backing of CAs, the value of SSL/TLS certificates is not just the physical mechanisms by which they encrypt data but in how they legitimise websites in the eyes of browsers and users, allowing for the seamless, safe web browsing experience people rely on every day.
