In this guide, we’ll explore what TLS (Transport Layer Security) is, how it works, and explain how it has advanced beyond the older SSL protocol to secure online transactions and protect sensitive data.
What is TLS?
TLS (Transport Layer Security) is the cryptographic protocol that ensures a secure, encrypted link between a web server and a user’s browser. This TLS connection safeguards any data exchanged—whether it’s login credentials, credit card information, or other sensitive details—so it remains confidential and protected from interception.
Replacing the original SSL protocol, TLS now sets the standard for secure online communication. However, the term “SSL” persists when referring to the digital certificates used to implement TLS on web servers. This is why the industry still advertises “SSL certificates”, despite the fact they are technically TLS certificates.
TLS encryption works through public key cryptography, which uses a pair of keys: a public key that’s openly shared and a private key that’s securely stored on the server. This key pairing helps establish a trusted and secure connection, making TLS an essential tool in giving everyday people the confidence to shop and manage sensitive information online.
A Brief History of TLS - How Did it Improve on SSL?
The history of TLS dates back to 1999, when it was introduced as a proposed Internet Engineering Task Force (IETF) standard to act as a successor to the Secure Sockets Layer (SSL) protocol, specifically SSL 3.0. The development of TLS actually began as SSL version 3.1, but the name was changed to TLS to signify its independence from Netscape’s SSL (the development of the original SSL protocol was led by the chief scientist at Netscape, Taher Elgamal, who is widely considered the “father of SSL”.)
The first version of TLS was published to address the security vulnerabilities inherent in SSL, such as:
- Lack of Message Integrity: SSL relied on outdated hashing methods, such as MD5, that were later found to be susceptible to attacks, potentially allowing hackers to alter or tamper with data in transit without detection. TLS introduced stronger hashing algorithms to ensure message integrity.
- Weak Cipher Suites: SSL-supported cipher suites were increasingly considered weak as encryption standards advanced. These weaker ciphers left data vulnerable to interception and decryption. TLS introduced the ability to use more robust cipher suites, such as those based on AES (Advanced Encryption Standard).
- No Protection Against Certain Downgrade Attacks: SSL protocols were vulnerable to downgrade attacks, where an attacker could force a connection to revert to a weaker encryption standard. TLS introduced mechanisms to prevent such attacks, helping to ensure that only the most secure encryption standards would be used.
- Insufficient Authentication of Messages: SSL’s message authentication used a method that combined both the message and its key, which was less secure. TLS improved this by implementing the HMAC (Hashed Message Authentication Code) system, which provided a stronger and more standardised approach to message authentication.
- Vulnerability to Man-in-the-Middle (MITM) Attacks: Historically, SSL did not have adequate protection against man-in-the-middle attacks, which allowed attackers to intercept and potentially alter data between the client and server. TLS introduced enhancements to the handshake process, making MitM attacks much more difficult to execute.
Over the years, TLS has evolved, with each new version providing enhanced security features to keep up with the most clever and persistent cybercriminals.
How Does TLS Work?
The TLS protocol functions in the same basic way as SSL, as described in our guide to SSL. The entire process revolves around the “handshake” between the client (your web browser) and the server (the website you are accessing).
This ‘TLS handshake’ authenticates both parties and secures the connection by agreeing on encryption methods and exchanging cryptographic keys. Here’s a detailed breakdown of how it works:
- Client Hello: The client (web browser) initiates the process by sending a “hello” message to the server, listing the supported encryption algorithms known as cipher suites.
- Server Response: The server responds by selecting an encryption algorithm and sending its TLS certificate, which includes a public key. This certificate is used to verify the server’s identity.
- Certificate Verification: The client verifies the server’s TLS certificate to ensure it is valid and issued by a trusted Certificate Authority (CA), such as DigiCert, Verokey, Comodo, etc.
- Key Exchange: The client generates a session key, encrypts it using the server’s public key, and sends it to the server.
- Session Establishment: The server decrypts the session key using its private key. Now, both the client and server share this session key, which encrypts and decrypts the data exchanged during the session. This session key is unique to the session (your website visit) and ensures that any data exchanged while you are there, like passwords and credit card information, is private and secure.
- Secure Connection Established: Once the session key is exchanged, the secure connection is established. The browser typically displays a padlock icon in the browser address bar to indicate the active, encrypted session.
This entire process happens almost instantly and without notice to most internet users. Compared with the original, outdated SSL handshake, the TLS handshake protocol leverages enhanced security features like Perfect Forward Secrecy (PFS), which became mandated in TLS 1.3 and onwards.
PFS means that each session generates a unique, temporary key. This ensures that even if one session key is compromised, it does not impact previous or future sessions, which was a vulnerability in the original SSL protocol.
Encryption in TLS - How Does it Work?
Encryption is the backbone of TLS, which leverages both symmetric and asymmetric encryption methods to secure the data transmitted between client and server applications. Both encryption methods rely on encryption algorithms like AES and RSA, which we will learn more about below.
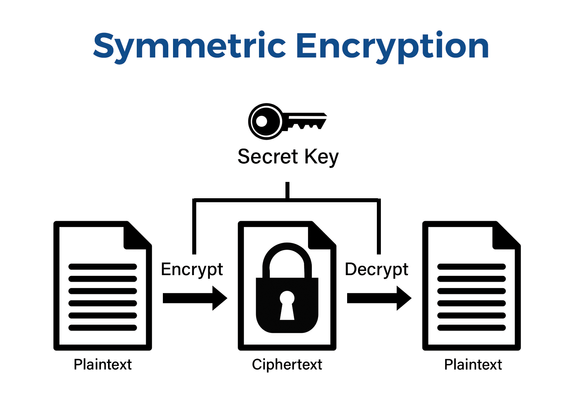
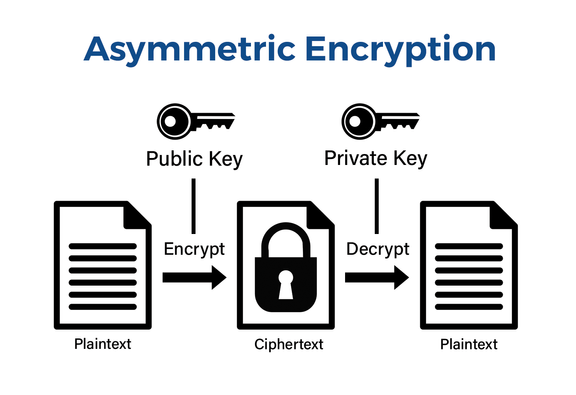
Symmetric vs Asymmetric Encryption
Symmetric encryption uses a single key for both encryption and decryption, making it faster and more efficient for encrypting large amounts of encrypted data. Common algorithms used include Advanced Encryption Standard (AES).
Asymmetric encryption employs a pair of keys: a public key for encryption and a private key for decryption. Common algorithms used include Rivest-Shamir-Adleman (RSA).
The primary distinction between the two lies in speed and complexity: symmetric encryption is faster, while asymmetric encryption provides enhanced security through key pairs.
So, why are both methods used in the TLS handshake?
Both are used to achieve a balance between speed and security.
The handshake starts with asymmetric encryption (pair of keys), where the client uses the server’s public key to encrypt a unique session key.
This approach ensures that only the server, with its private key, can decrypt this initial communication, securing the exchange of the session key. Although asymmetric encryption is highly secure, it is also slower, so it is used only for this initial key exchange stage.
Once the session key is securely shared, TLS switches to symmetric encryption, where the same session key encrypts and decrypts all subsequent data. Symmetric encryption is much faster, making it ideal for efficiently securing large amounts of data in real-time communication.
So, by combining the strengths of both methods, TLS achieves a secure, high-performance connection. In short, asymmetric encryption protects the sensitive initial key exchange, while symmetric encryption enables rapid data transfer, achieving an equilibrium where the connection is both secure and responsive.
Ensuring Data Integrity with HMAC
Alongside the two encryption methods described above, TLS employs HMAC (Hash-Based Message Authentication Code) to ensure data integrity.
But why is this necessary if the data is already encrypted?
While encryption protects the confidentiality of data, it does not inherently safeguard against tampering.
Encryption methods, whether symmetric or asymmetric, ensure that only authorised parties can view the data, but they do not detect or prevent modifications during transmission.
This is where HMAC comes in: HMAC uses a combination of a secret key and a cryptographic hash function to verify the authenticity and integrity of each message exchanged. When data is sent, an HMAC is generated and attached to it, acting like a unique digital signature. When the data is received, the recipient generates its own HMAC and compares it to the original. If the two match, it confirms that the data has not been altered in transit.
What is a TLS Certificate?
Think of a TLS certificate as a digital ID card for a website, proving that the site is trustworthy and legitimate. When you visit a secure website, the TLS certificate is how your browser knows it is safe to connect.
Here’s how it works and how it’s created:
- What is a TLS Certificate, exactly? It’s a file stored on the web server that includes information such as the website’s name, its public encryption key, and details about who issued the certificate.
- How is it Created? The website owner generates a unique pair of encryption keys—a public key and a private key. The public key is shared, while the private key is kept secret. The public key included in the certificate is used by visitors’ browsers to verify the server’s identity and engage in the TLS handshake, setting up the encrypted connection.
- How is it Issued? To obtain a TLS certificate, the website owner applies to a trusted Certificate Authority (CA), such as DigiCert, Verokey, Comodo, etc. The CA then engages in a process known as business validation, where they check the website owner is who they say they are and that they have a legitimate website. Once verified, the CA issues the certificate, essentially “signing off” that the website is authentic.
Conclusion: The Cutting Edge of Website Security
TLS and its successive iterations form the backbone of website encryption, ensuring that sensitive information like passwords, credit card numbers, and personal details stay confidential and protected from interception by bad actors. While “SSL” is still the dominantly used term, TLS is the true hero behind the web security we all rely on.
